Step 1:CYBERATOR
Download Following Tools and Scripts:
Cain and Abel(http://www.oxid.it/cain.html)
Wireshark (http://www.wireshark.org/download.html)
Mozilla Add-ons : GreaseMonkey (Search in Mozilla add-ons)
Cookie Injector Script (http://userscripts.org/scripts/source/119798.user.js)
Wireshark (http://www.wireshark.org/download.html)
Mozilla Add-ons : GreaseMonkey (Search in Mozilla add-ons)
Cookie Injector Script (http://userscripts.org/scripts/source/119798.user.js)
Step 2:
Open Cain & Abel
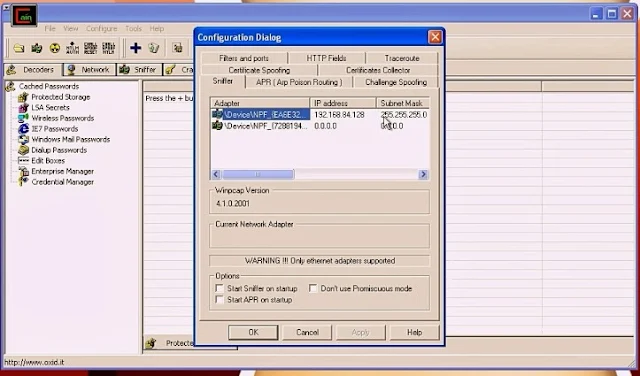
Navigate to “Configure” menu and open configuration Dialog and check the configuration settings…
Step 3:
Click on (Start/Stop) Sniffing button.
Click
 tab.
tab.Click on
 button.
button.
Now, the following window will appear….
Now Click on OK button…..Scanning Starts
Step 4:
Click on Button, a pop-up window will appear.
Button, a pop-up window will appear.
Now Select the IP Address of the victim from the left panel of window and the Router IP in the right panel…..as shown below:
Click OK button.
Step 5:
Select the IP in the table.Click on
 button.
button. Step 6: On the Victim’s PC:
Start any Browser and open facebook.com (force Http)
Step 7: Now Back to Attacker’s Pc
Open Wireshark
Navigate to Capture>Interface (or press Ctrl+I)
Select your active wireless adaptor
Navigate to Capture>Interface (or press Ctrl+I)
Select your active wireless adaptor
Step 8:
Refresh victims Facebook page
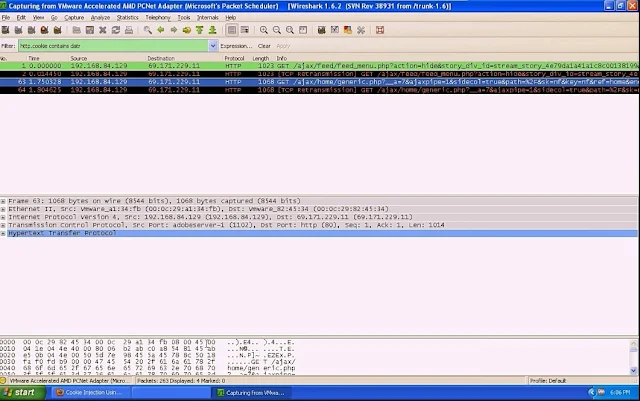
Open your Wireshark window, now you can see the flow of packets
Type “http:cookie contains datr” in the filter box.
Click on button.
button.
Open your Wireshark window, now you can see the flow of packets
Type “http:cookie contains datr” in the filter box.
Click on
Search for “Generic.php” or “ai.php”
Right click on the particular packet then select “copy>bytes>Printable Text Only”.
Right click on the particular packet then select “follow TCP Stream”.
Open up your browser, open http://www.facebook.com.
Press Alt+C (small wireshark cookie dump will appear).
Paste the cookie that we copied earlier (Ctrl+v).
Press OK.
Right click on the particular packet then select “copy>bytes>Printable Text Only”.
Right click on the particular packet then select “follow TCP Stream”.
Open up your browser, open http://www.facebook.com.
Press Alt+C (small wireshark cookie dump will appear).
Paste the cookie that we copied earlier (Ctrl+v).
Press OK.
Now reload the page….
We have the Session now…. :)








this is rajasekar @ ramco institute of technology.
ReplyDeleteplease send me ur mail id sir---my mail id is "dhevasekar2@gmail.com"
your way to facebook crack was so good....