Vulnerability scanning using NSE in Nmap.
Note: I have written this tutorial taking the fact into consideration that the user is well versed with basic NMAP commands.
For basic NMAP commands please refer the cheat-sheet given below:
Basic Scanning Techniques
• Scan a single target : nmap [target]
• Scan multiple targets: nmap [target1,target2,etc]
• Scan a list of targets nmap -iL [list.txt]
• Scan a range of hosts nmap [range of IP addresses]
• Scan an entire subnet nmap [IP address/cdir]
• Scan random hosts nmap -iR [number]
• Excluding targets from a scan nmap [targets] –exclude [targets]
• Excluding targets using a list nmap [targets] –excludefile [list.txt]
• Perform an aggressive scan nmap -A [target]
• Scan an IPv6 target nmap -6 [target]
Discovery Options
• Perform a ping scan only nmap -sP [target]
• Don’t ping nmap -PN [target]
• TCP SYN ping nmap -PS [target]
• TCP ACK ping nmap -PA [target]
• UDP ping nmap -PU [target]
• SCTP Init Ping nmap -PY [target]
• ICMP echo ping nmap -PE [target]
• ICMP Timestamp ping nmap -PP [target]
• ICMP address mask ping nmap -PM [target]
• IP protocol ping nmap -PO [target]
• ARP ping nmap -PR [target]
• Traceroute nmap –traceroute [target]
Firewall Evasion Techniques
• Fragment packets nmap -f [target]
• Specify a specific MTU nmap –mtu [MTU] [target]
• Use a decoy nmap -D RND: [number] [target]
• Idle zombie scan nmap -sI [zombie] [target]
• Manually specify a source port nmap –source-port [port] [target]
• Append random data nmap –data-length [size] [target]
• Randomize target scan order nmap –randomize-hosts [target]
• Spoof MAC Address nmap –spoof-mac [MAC|0|vendor] [target]
• Send bad checksums nmap –badsum [target]
Version Detection
• Operating system detection nmap -O [target]
• Attempt to guess an unknown OS nmap -O –osscan-guess [target]
• Service version detection nmap -sV [target]
• Troubleshooting version scans nmap -sV –version-trace [target]
• Perform a RPC scan nmap -sR [target]
Nmap Scripting Engine
• Execute individual scripts nmap –script [script.nse] [target]
• Execute multiple scripts nmap –script [expression] [target]
• Execute scripts by category nmap –script [cat] [target]
• Execute multiple scripts categories nmap –script [cat1,cat2, etc]
• Troubleshoot scripts nmap –script [script] –script-trace [target]
• Update the script database nmap –script-updatedb
__________________________________________________________________________________
NSE Script- Vulscan
Requirements:
OS: Windows 10
NMAP - DOWNLOAD
Vulscan Script - DOWNLOAD
STEP 1:
Download and install Nmap for windows from the above given link.
Check if nmap is working or not by typing the following command in power shell:
nmap -h
STEP 2:
Download the Vulscan script.
Navigate to the Scripts folder in NMAP installation directory and make a new folder with the name vulscan
Paste the extracted Vulscan script in vulscan folder.
STEP 3:
Select any target to scan for vulnerability.
Open power shell and execute the following command:
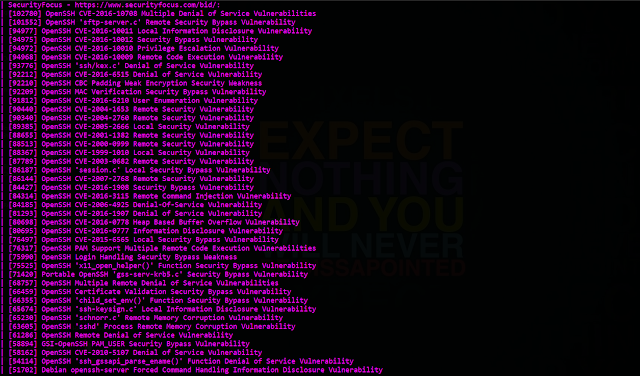
nmap -sV --script=vulscan/vulscan.nse www.fcibank.com.pk
It will list all the vulnerabilities present in the target. Now you can use METASPLOIT for further exploitation. ☺
STEP 4:
Update Database
The vulnerability databases are updated and assembled on a regularly basis. To support the latest disclosed vulnerabilities, keep your local vulnerability databases up-to-date.
If you want to update your databases, go to the following web site and download these files:
https://www.computec.ch/projekte/vulscan/download/cve.csv
https://www.computec.ch/projekte/vulscan/download/exploitdb.csv
https://www.computec.ch/projekte/vulscan/download/openvas.csv
https://www.computec.ch/projekte/vulscan/download/osvdb.csv
https://www.computec.ch/projekte/vulscan/download/scipvuldb.csv
https://www.computec.ch/projekte/vulscan/download/securityfocus.csv
https://www.computec.ch/projekte/vulscan/download/securitytracker.csv
https://www.computec.ch/projekte/vulscan/download/xforce.csv
Copy the files into your vulscan folder:
/vulscan/
Nmap script categories
| Nmap Script Name | Description |
|---|---|
| auth | All sorts of authentication and user privilege scripts |
| broadcast | Network discovery scripts that use broadcast petitions for intel gathering |
| brute | Set of scripts for performing brute force attacks to guess access credentials |
| default | The most popular Nmap scripts, using -sC by default |
| discovery | Scripts related to network, service and host discovery |
| dos | Denial of service attack scripts used to test and perform DOS and floods |
| exploit | Used to perform service exploitation on different CVEs |
| external | Scripts that rely on 3rd party services or data |
| fuzzer | Used to perform fussing attacks against apps, services or networks |
| intrusive | All the ‘aggressive’ scripts that cause a lot of network noise |
| malware | Malware detections and exploration scripts |
| safe | Safe and non-intrusive/noisy scripts |
| version | OS, service and software detection scripts |
| vuln | The Nmap vuln category includes vulnerability detection and exploitation scripts |







Very informative...
ReplyDeleteThanks ☺
Deletevery useful and informative. Thank you.
ReplyDeleteThanks sir ji
ReplyDelete